
👾🔐 Think VPNs are top for remote access? Think again! Explore Multi-Factor Auth, Zero Trust, and JIT with #FudoSecurity ! 🚀🔒
Learn more: ➡ fudosecurity.com
#CyberSecurity #ZeroTrust #JustInTimeAccess

🕸️👾 Overwhelmed by remote access management options? Our 'Compliance USA' e-book is your guide through the maze! 📘🚀
📥 Download now: bit.ly/USA_Compliance
#RemoteAccess #ZeroTrust #JITaccess


🔏 We’ve released the Encrypted DNS Implementation Guidance. This document aims to equip federal civilian executive branch (FCEB) agencies with actionable guidance on implementing encrypted DNS protocols that conform to the Federal #ZeroTrust Strategy. go.dhs.gov/33g


Diode partner 0Loop (@JamesTervit) demo of media streaming over the #zerotrust backbone #blockchain . Join the tg channel for cool stuff like this: t.me/diode_chain

¿Es posible reforzar la seguridad de la red sin añadir complejidad? es posible, implementando una estrategia #ZeroTrust en el acceso con #ExtremeCloud #UniversalZTNA . +info: extremenetworks.com/resources/blog…


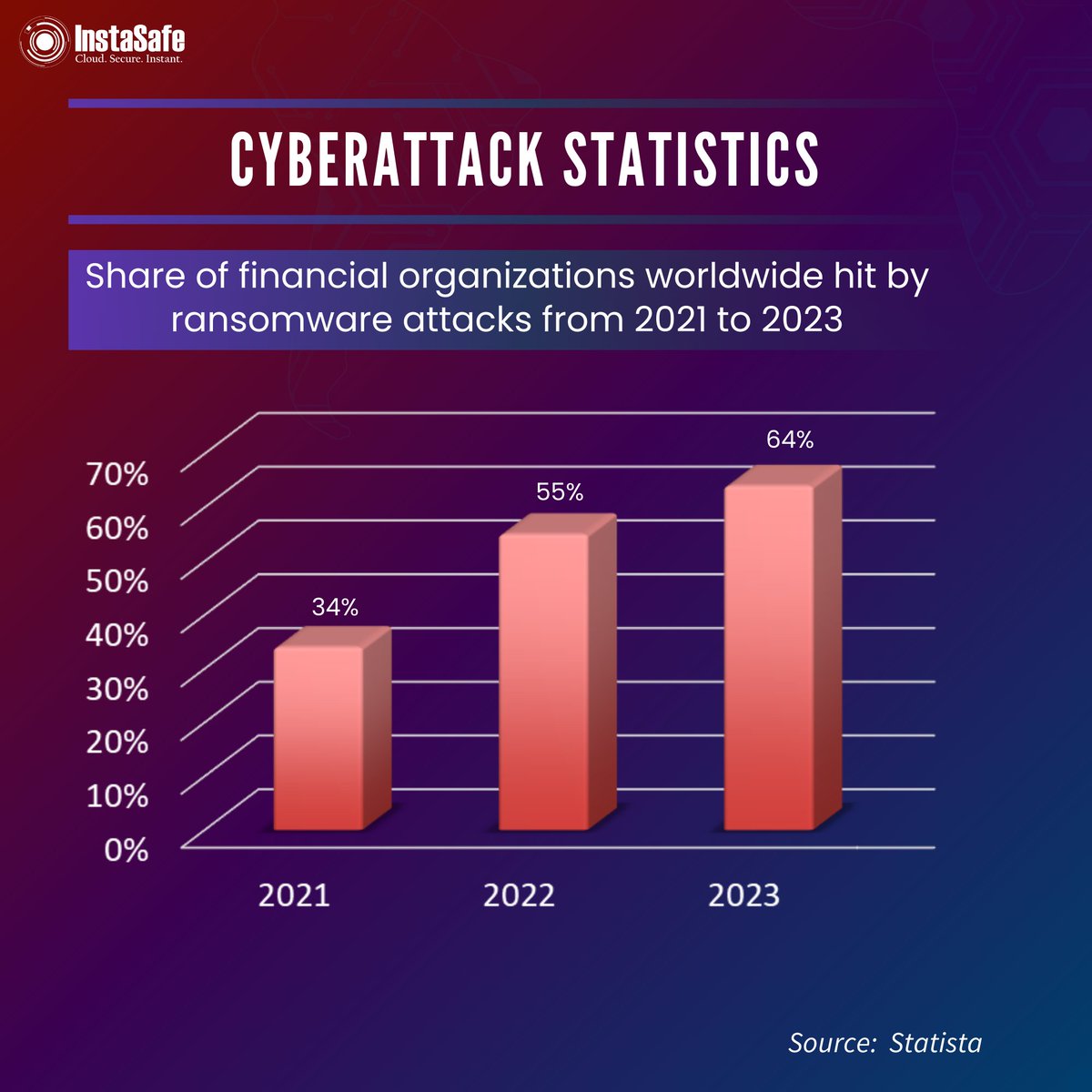
💰 Ransomware hits hard: The share of financial organizations worldwide affected by attacks surged from 2021 to 2023.💳🔒
With cyber threats escalating, safeguarding financial data is paramount.
#CyberSecurity #Ransomware #CyberStats #ProtectYourData #ZeroTrust #InstaSafe

Going to #Veeam ON 2024? Make sure you get Object First on your dance card! Read this exclusive @VMblog Q&A with Anthony Cusimano to get a sneak peek at what they have planned for the show. vmblog.com/archive/2024/0…
#Veeam #Storage #ransomware #ZeroTrust #ZTDR #Ootbi




Wie schützen IT-Abteilungen im #Gesundheitswesen Ihr #Netzwerk ? Jetzt zum Webinar anmelden und mehr erfahren über #Cybersecurity und #ZeroTrust mit Alcatel-Lucent Enterprise #WhereEverythingConnects #Healthcare #NIS2 #KRITIS bit.ly/4bZoKRB


EDIX東京(教育総合展)EDIX(教育総合展) 最終日は朝から良いお天気です!
皆様のご来場をお待ちしています。
#EDIX 東京 #EDIX #ITセキュリティ #RevoWorks #zerotrust



#ZeroTrust is a business imperative for our partner Blackwood. So, we've worked together to ensure our mutual customers have the high-fidelity visibility needed to succeed on the Zero Trust journey.
Hear more from Blackwood CTO Christopher Ebley:
ow.ly/l89x50RGlvB


John John Kindervag putting on a #ZeroTrust clinic at our booth. Making Zero Trust easy! #RSAC


#GenerativeAI is a powerful force, but in the wrong hands, can become a potent #cyber weapon. So how can you fortify your defenses against AI-powered #cyber attacks? Read new #networksecurity #blog to learn why #ZeroTrust Network Access is the way to go: bit.ly/4d8Ahzb


Zero trust is a #strategy , not a technology
buff.ly/3Qo8gd3
ComputerWeekly #tech #zerotrust #cybersecurity #security #cyberstrategy #identity management #IAM #cyberthreats #cyberattacks #business #leadership #management #CISO #CIO #CTO #identity #networksecurity






