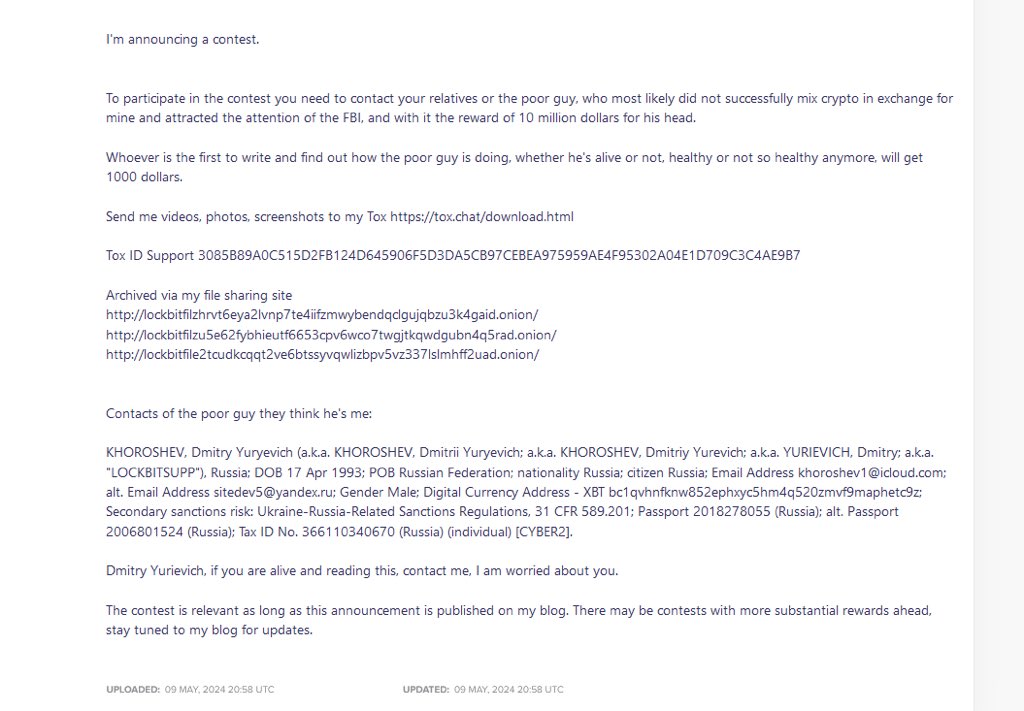
krebsonsecurity.com/2024/05/how-di…
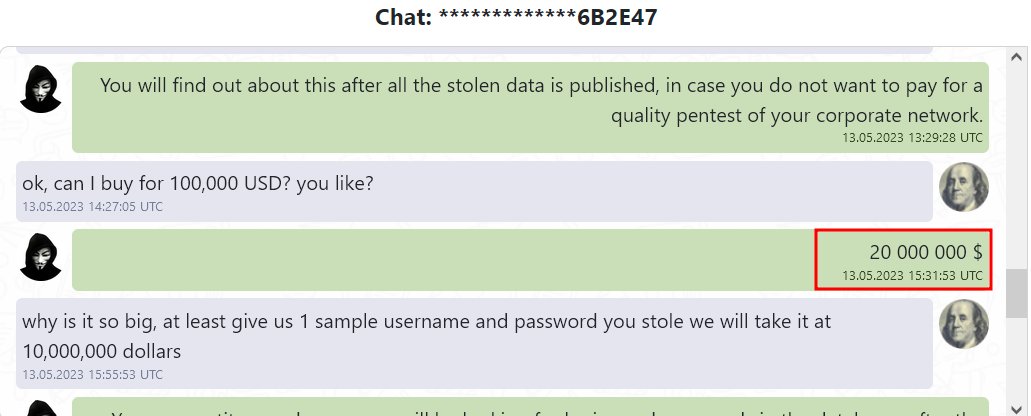
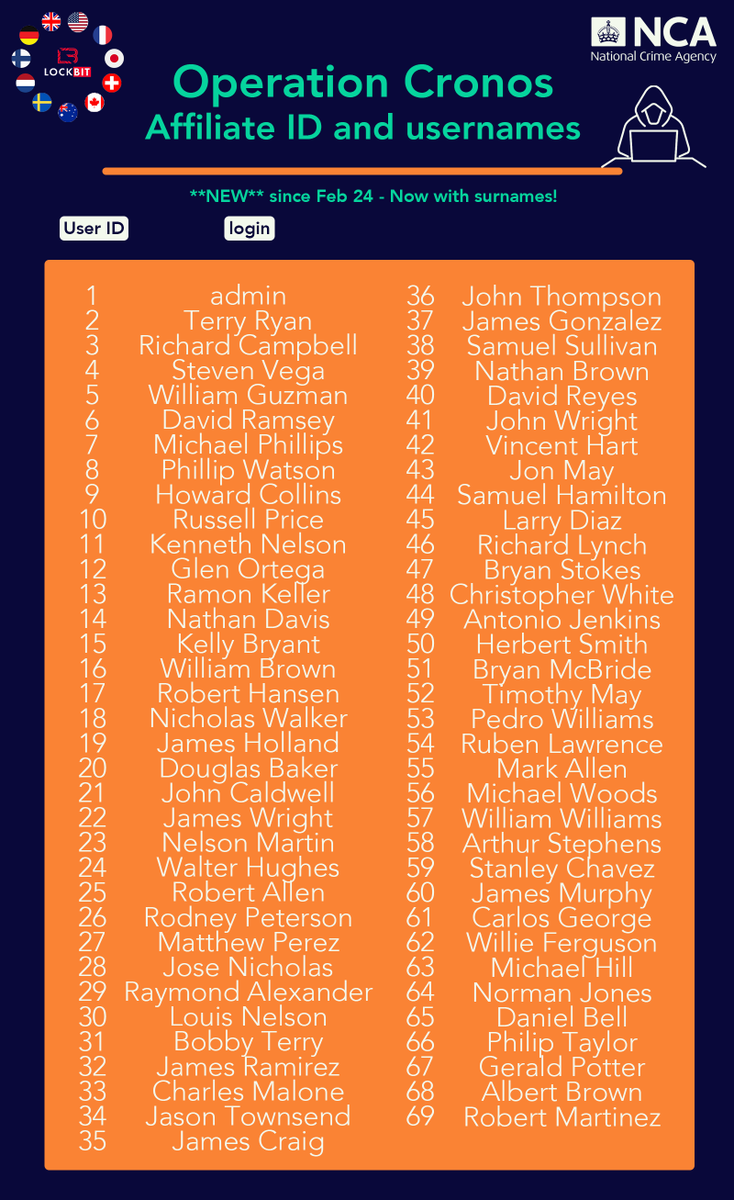
'But given that LockBitSupp has been actively involved in Lockbit ransomware attacks against organizations for four years now, the government almost certainly has an extensive list of the LockBit leader’s various cryptocurrency addresses — and probably



Interesting.. Anonymous Egypt links back to STORMOUS blog with a breach, but they are forwarding LockBit messages inside of their channel. So are they affiliate of both?
#DarkWeb Informer #DarkWeb #Cybersecurity #Cyberattack #Cybercrime #Infosec #CTI #Ransomware

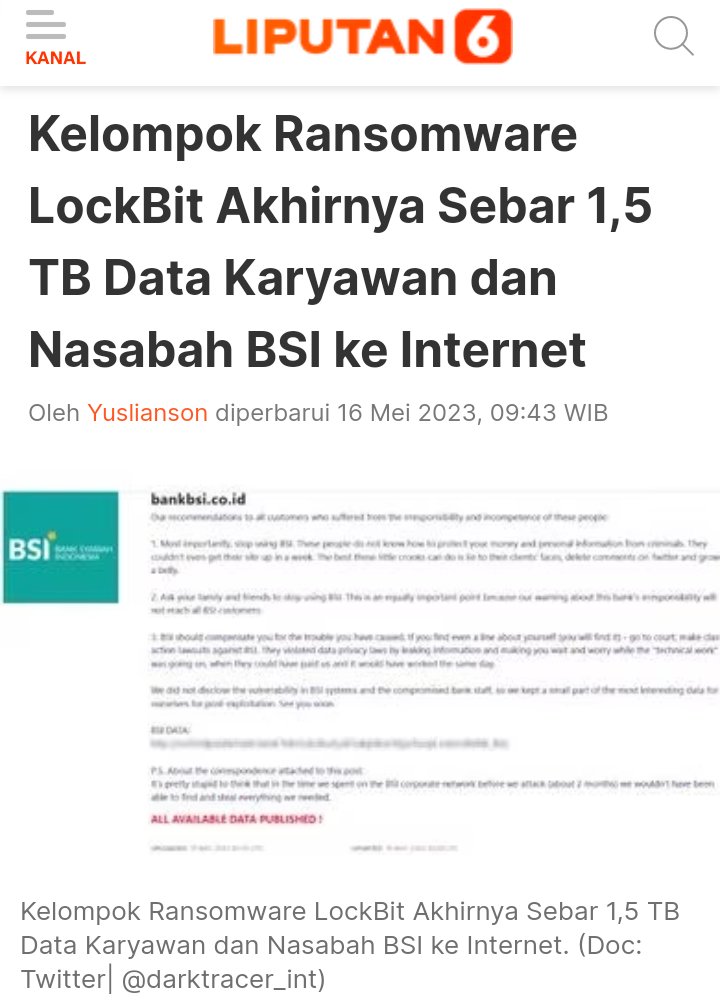
🚨Wow, some BIG breaches.
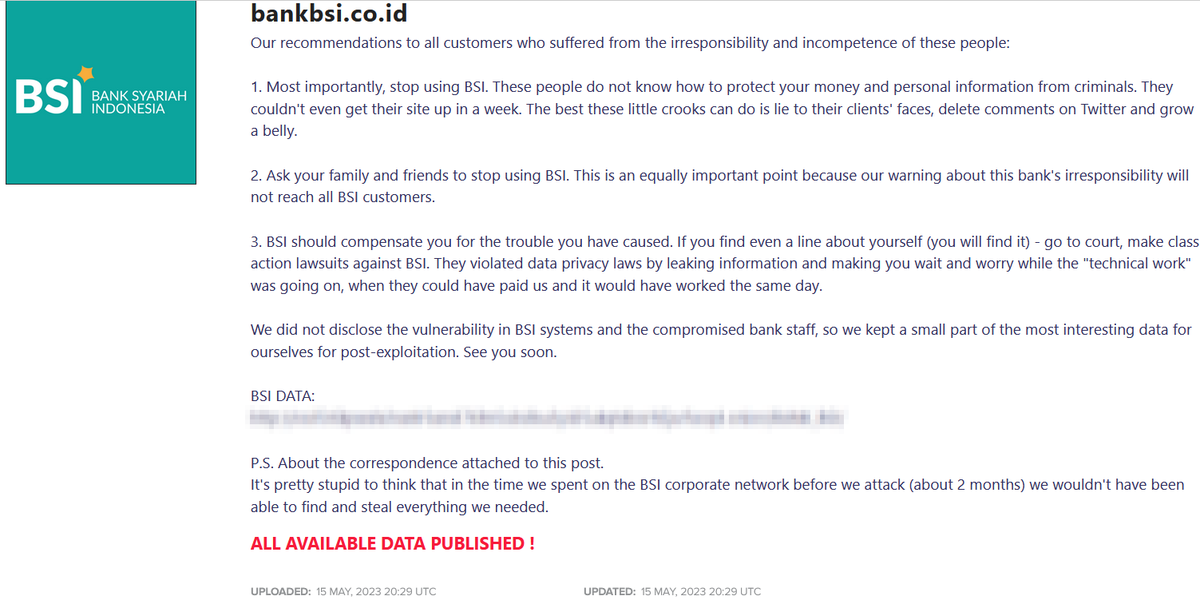
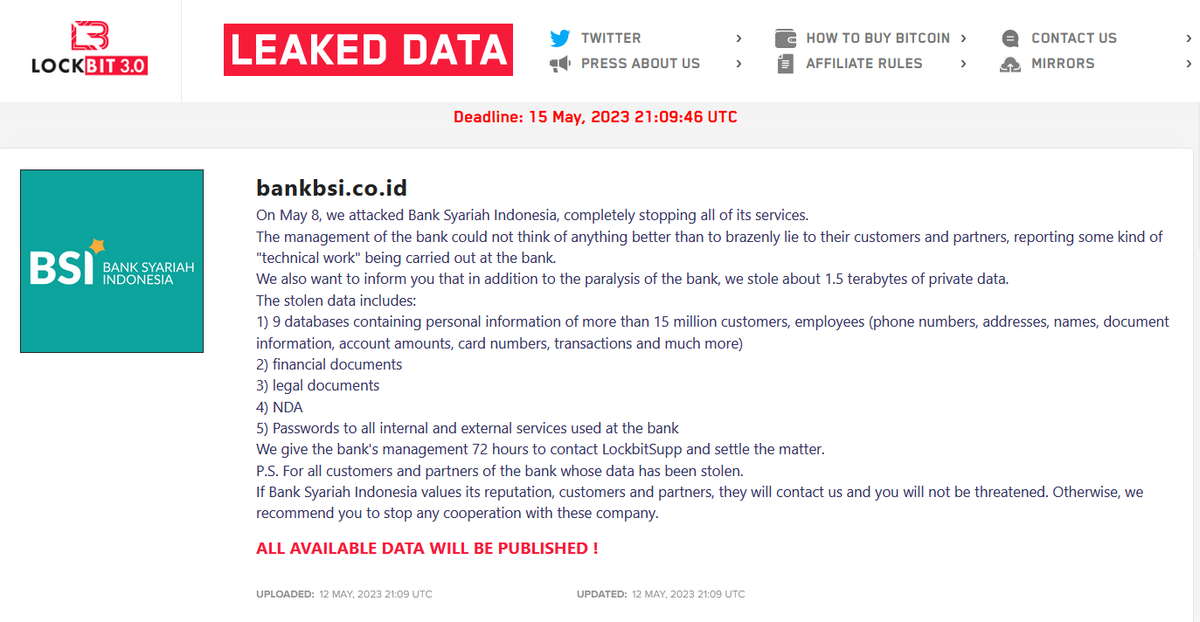
⚠️ #Ransomware ⚠️Allegedly, #LockBit has named multiple victims.
#DarkWeb #Cybersecurity #Security #Cyberattack #Cybercrime #Malware #Privacy #Infosec
Threat Actor: LockBit
Ransomware Victim: 4 Victims
Date: 2024-05-15
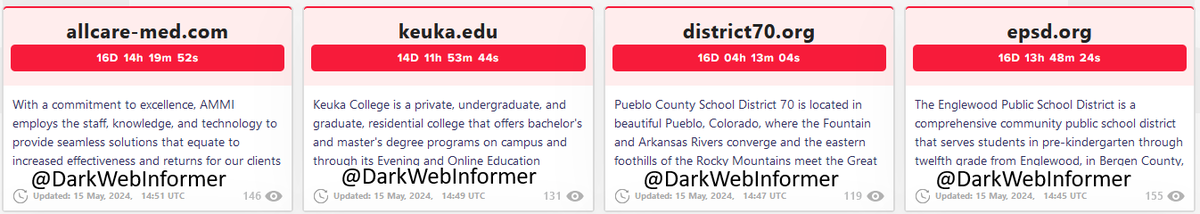



LockBit is still posting.
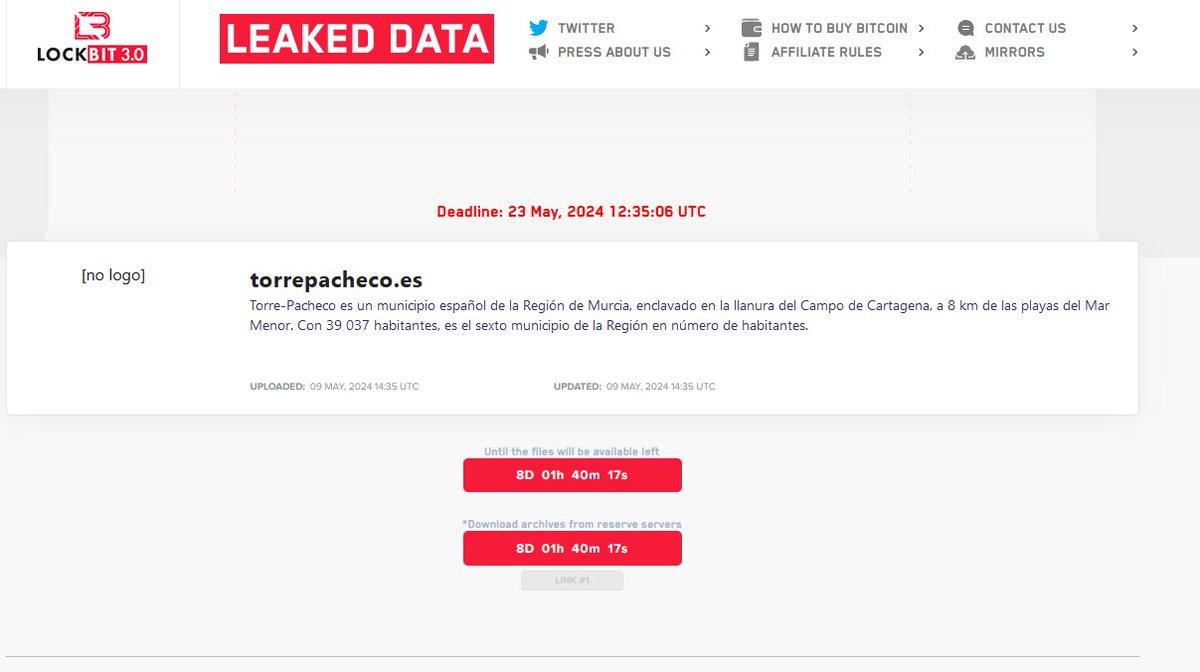
⚠️ #Ransomware ⚠️Allegedly, #LockBit has named multiple victims.
#DarkWeb Informer #DarkWeb #Cybersecurity #Cyberattack #Cybercrime #Malware #Infosec #CTI
Threat Actor: LockBit
Ransomware Victim: 80+ Victims
Date: 2024-05-09